Tuesday, January 3, 2012
Linux on the Cloud { even from Microsoft }
Now, surprisingly, Microsoft is preparing to launch a new persistent virtual machine feature on its Azure cloud platform, enabling customers to host Linux, SharePoint and SQL Server there. However, it will be up to customers to provide uploads of their own Linux images.
Click here for a brief overview of Microsoft Azure
Click here for a brief overview of Amazon EC2
Click here for a brief overview of [Linux] Cloud computing with Ubuntu
Click here for a brief overview of [Linux] Cloud computing with Red Hat
Click here for a brief overview of [Solaris] Cloud computing with Oracle
Tuesday, December 6, 2011
The Personal Computer Is Dead ?
Saying that the personal computer is dead may or may not be premature. However, I just read an article that makes this assertion, and I'd like to suggest that you read it too.
Click here to read The personal computer is dead by Jonathan Zitttrain. He says in conclusion,
"A flowering of innovation and communication was ignited by the rise of the PC and the Web and their generative characteristics. Software was installed one machine at a time, a relationship among myriad software makers and users. Sites could appear anywhere on the Web, a relationship among myriad webmasters and surfers. Now activity is clumping around a handful of portals: two or three OS makers that are in a position to manage all apps (and content within them) in an ongoing way, and a diminishing set of cloud hosting providers like Amazon that can provide the denial-of-service resistant places to put up a website or blog."
Saturday, December 3, 2011
For users of iPhones, Blackberries, Androids and/or Skype
We live in an age that's nothing short of Orwellian.
There's a new industry that secretly vacuums up your data and preserves it forever on high-end servers that hold many petabytes (a million gigabytes) of information.
WikiLeaks has just released the Spy Files – a trove of almost 300 documents from these companies that shine a light into this industry.
One, a brochure from SS8 of Milpitas, California, touts its Intellego product that allows its owner to see (in real time, if it wants) such things as your draft-only emails, attached files, pictures and videos.
State agencies have expanded their data-collecting to include data on water and sewage billing, visitor logs from parks and recreation facilities and much more.
To read more about this subject, click here for Wikileaks: The Spy Files 2011-12-01
NB: Several posts to this blog have been on the subject of security. I feel that The Spy Files need to be part of any consideration of this subject.
= = = = = = = = =
It turns out that spyware is running on hundreds of millions of smartphones and tablets.
The carriers explain their use of this spyware program in a way that makes it sound harmless. However, it only sounds harmless until you see, among other things, that it is capturing your every key stroke.
With iPhones, which have the program in them, turning off the spyware program is sometimes easy.
If you’re running iOS 5.x, just head to:
Settings > General > About > Diagnostics & Usage
and click “Don’t Send” on.
If you’re running iOS3 or 4, however, I don’t know of any current way to disable the service.
With Android phones, it’s much trickier, but it can be done. The story on BlackBerries is a bit murky.
Hopefully, because this practice has received a lot of attention recently, the carriers will soon make it simple to disable this spyware for those of you who don’t want to share everything you do on your phones with your phone companies.
Tuesday, November 15, 2011
Search Engines and The Data Explosion
In trying to scale to meet this data explosion, our search engines are getting creaky.
While Google has been busy working on building Google+ as its social tool, Microsoft has quietly gone out and cut partnership deals with Facebook and Twitter and started integrating their social data into Bing search results. For example, if you do a search on Bing and you’re logged into Facebook in the same browser then the search results will show which of your friends have liked a certain page. See the example below:

Bing may have a leg up on Google in social today because of the Microsoft deals with Facebook and Twitter, but you also have to keep in mind that Google is going to have more control over its social-search destiny by building its own product. It won’t have to worry about partnership deals going bad or having to ask its social partners for additional API access. Google can just make it happen.
Wednesday, November 9, 2011
An Open Standard - HTML5, Yes; Flash, No
It's a win for Apple Inc., which has famously banned Flash from working on the iPhone and the iPad.
The mobile era is about low power devices, touch interfaces and open web standards - all areas where Flash falls short.
HTML5’s video chief rival, Adobe Flash, appears to be throwing in the towel.
HTML5 is now universally supported on major mobile devices, in some cases exclusively.
This makes HTML5 the best solution for creating and deploying content in the browser across mobile platforms.
The writing may be on the wall. While Adobe programmers will be able to use their same Adobe software development tools, the end-product is clearly going to be HTML5 video. Flash may now be a legacy format.
Silverlight? Microsoft’s one time rival to Flash? It may be toast. The day of non-standard video formats seems to be coming to an end.
Note 1: Adobe is working on Flash Player 12 and a new round of features which they expect to again advance what is possible for delivering high definition entertainment experiences … to the desktop, not to mobile devices.
Note 2: Flash is not an open standard — it is controlled by Adobe Systems — whereas HTML5 is largely controlled by a committee made up of three companies, one of them being Apple.
Click here for an 11/11/11 Wall Street Journal front-page article on HTML5.

Developers now have to consider three development environments to address desktop and mobile device access: 1). traditional Websites using Flash for desktop and laptop access, 2) mobile-optimized Websites using HTML5 for mobile-device Web access, and 3) mobile-application development that may interact with Web resources on the back end.
Adobe is now focusing its mobile developer solutions on Adobe Integrated Runtime (AIR) that helps developers use Flash technology and develop apps that will run across multiple mobile platforms such as iOS, Android, BlackBerry and Windows Phone.
Monday, September 19, 2011
Webkit-Based Development Revisited
I've made references to Webkit-based technologies in prior posts to this blog and in some early articles. For example,
Click here (2011) and here (2008).
I've also been referring to HTML5 of late. For example,
Click here and here
And way back, I've referred to A/B testing. For example,
Click here (2009)
For a presentation from NetFlix that pulls together these and other related topics,
Click here. The download of this 7 MB pdf file may take awhile if you have a slow connection.
Comment: While you may not be working on a project exactly like the one the authors discuss, you may find its information interesting nonetheless. I did.

As the default browser for both iPhone and Android, WebKit has become a major player in the mobile arena, offering a wider array of HTML5 and CSS3 support than any other major engine. For a soon-to-be-available book, see

This book gets you started with WebKit and shows you how to maximize HTML5 and CSS3 features in WebKit, and it addresses ways to optimize your web site for mobile devices and enhance the mobile user experience.
Thursday, September 8, 2011
Speech Recognition With General and Medical Vocabularies Revisited II
A Google search on “mba md programs” brings back over 12 million results, many of which are the particulars of the hundreds of MD/MBA programs now offered by leading universities.
This means that medical practices are now incorporating modern business models and that, in turn, means that practice managers and their accountants are not only looking for ways to cut costs as they have in the past but are now also looking for ways to establish new profit centers. Many times, speech-to-text tools like Dragon Medical Practice Edition provide the solution to one or both.
Nuance will this month release Dragon Medical Practice Edition, an upgrade to its medical speech recognition tool for small offices that should even further reduce transcription costs by making it easierier to enter data into an EHR.
Dragon Medical Practice Edition is similar to Nuance's existing Dragon speech recognition options for health care in that it allows health care workers to create medical notes directly in an EHR system in real time.
The new version has a number of time-saving features: for example, it alerts the user and offers advice when a poor audio input caused by incorrect microphone connection or background noise is detected. And that’s just the beginning.
Existing and new users can click here for the results of a YouTube search on “Dragon Medical Practice Edition”
These voice-translation videos fall roughly into the following three categories:
• Technical topics such as profile optimization
• Nuance and other tutorials
• Case studies narrated by practicing physicians
These YouTube videos and my prior posts on speech-to-text translation offer a pretty comprehensive introduction to speech recognition software in general and Dragon Medical software in particular. Check them out.
Tuesday, August 30, 2011
Speech Recognition With General and Medical Vocabularies Revisited
A while ago, back on May 10, 2009, I posted an article that discussed speech recognition software in general and Dragon Medical 10 in particular. Click here to navigate to that post. In the two years plus since then, the field of speech-to-text translation (and the hardware available for speech-to-text translation software to execute on) has advance. This can be seen in the research reports published at the Special Interest Sites that you can navigate to from the links at the top of the right-hand column of this blog.

Reflecting these advances, Vendors, Nuance Communications Inc., the maker of Dragon NaturallySpeaking and Dragon Medical Practice Edition, in particular, have been able to release improved versions of their products: The next version of Dragon Medical will be called “Dragon Medical Practice Edition” and will feature the Dragon NaturallySpeaking 11.5 Speech Engine. I have found it to be faster and more accurate than any previous version of Dragon. (The most recent versions utilize new hardware features such as multithreading and multicore CPUs, and they double the sampling rate and more).
That said, it's still important that you use any speech-to-text translation product with a good sound card and a good microphone.
Click here for a downloadable Product Sheet
Click here for a Feature and Specs Sheet
As is my wont, I recently installed a pre-release copy of Dragon Medical Practice Edition hurriedly: that is, I wasn’t very careful when I built a profile (trained Dragon) and then gave Dragon an initial test run by speaking into a 10-year-old, $5.95 microphone that happened to be connected to my sound card at the time. The idea was simply to familiarize myself with this new edition a little before using it seriously later. To my astonishment, even with this primitive set up, Dragon Medical Practice Edition converted my speech to text without a single error throughout a 5-minute run (using the General vocabulary).
There's an awful lot of information about this new version to sift through. Nuance's site (click here) is a good place to start.

{ Click on the image above for a larger view }

As a footnote, I want to add that systems that convert spoken words to text are not just of value to professional practices. I have an acquaintance who has used this software for over a year as he has had a stroke and finds it difficult to type. He speaks well of it.
Friday, August 19, 2011
Security Requirements for Electronic Health Records Redux
Click here for a commercial white paper on the title subject from the vendor Symantec. Although much of its content appears in earlier posts to this blog, this white paper presents a good summary of today's conventional wisdom on the subject.
Counter views abound, however. For example, many believe that there is no such thing as cybersecurity. That’s because no system can be 100% secure. There is no uncrackable code.
Wednesday, August 17, 2011
Google+ ... The next big thing ?

The following numbers are impressive, given that Google+ marketing hasn't yet begun.

It will be fascinating to see whether Facebook, which has a very big head start and hundreds of millions of satisfied users, or Google+, now only a few weeks old, which, once you get a free Google+ account, has a spot on the new, nearly ubiquitous, black Google toolbar, reaches a billion users first. Note: Each time you connect with any of the Google services (a billion people do each month), you see this new toolbar across the top of your browser.

Stay tuned ….
And/or click here for more overview.
Friday, August 5, 2011
The Changing Landscape For HTLM5 Design
Adobe Edge Preview is a new Web motion and interaction design tool that allows designers to bring animated content to websites, using web standards like HTML5, JavaScript, and CSS3.
The initial version of Edge focuses primarily on adding rich motion design to new or existing HTML projects, that runs beautifully on devices and desktops.
Click here to download your own copy of this free beta and examine the samples for yourself. With them, you can be up and running in only a few minutes, or click here to see an image of one of these samples that I've run on my desktop, or click here for one video that shows Edge in use and/or here for another.

{ Click on the image above for a larger view }
As much as we can give Apple credit for getting the HTML5 ball rolling, Adobe's decision to offer an HTML5 design tool is unlikely the result of Adobe giving in to Apple. It is a reasonable business decision that answers to a global trend - a decision that is driven rather by opportunity than surrender.
Few of us paid attention to this new format before Apple said it would deny Flash access to its iOS platform for performance, security and power consumption reasons (while others claim it is really the closed platform approach that killed Flash on iOS).
Within two years, HTML5 has evolved from an Apple thought process to a global movement with the conviction that HTML5 will be the future standard of how Web applications will be developed. It is a conviction that is shared by those who follow corporate interests as well as those who have the open Web in mind, such as Mozilla. Whether we like it or not, HTML5 will become a powerful application layer for the Internet within a few years - the first application layer that will enable Internet applications and services that will look and feel like desktop applications today.
Adobe sees Edge as a tool designers can use along with its Creative Suite applications such as Photoshop and Dreamweaver (discussed on a few of my earlier posts to this blog), although direct import support isn’t available yet. Adobe does, however, have plans to add import support as development continues.
Edge-created content is viewable on any HTML5-aware browser, such as Safari, Firefox and Chrome, and works on mobile devices such as the iPhone, iPad, HP’s WebOS, and Android-based smartphones.
The beta is still in its early stages, so it isn’t feature complete yet, and Adobe plans to use feedback from customers in the development process.
If you look at the market share for browsers, you will find that less than half the browsers in use are HTML5 compatible at this point. That percentage is certain to rise rapidly over the next couple of years, but a substantial share of the browser market will require an alternative to HTML5 for the foreseeable future. Companies will still need to be backwards compatible for older browsers at a minimum and will employ Flash for this.
In addition to raw browser support, HTML5 lacks a number of features that Flash offers. Most notably, Flash includes digital rights management (DRM) features, while in HTML5, users can quickly save videos to their own machines. That may not sound like such a bad thing for users, but for developers and content owners, it's a serious problem. A number of DRM schemes are currently under consideration for HTML5, but the issue is far from resolved. The best-fitting software depends on your use case. Many projects will benefit from technologies like Flash that are not browser controlled, for some time to come.
Adobe to Capitalize on The Rise of HTML5
While Flash has been the dominant technology used to create interactive, animated content, its market share has been decreasing as HTML5 gains ground. Apple refused to support Flash on the iPhone and the iPad citing performance issues (as noted above), which led many developers to move to adopt HTML5.
With PC sales dropping and tablet sales showing tremendous growth, many developers will eventually move on to HTML5 to create content as it is compatible with most platforms and doesn’t need any special plugins.
With Adobe Edge, Adobe plans to capitalize on this shift to HTML5. With Edge, Adobe can recapture some of its lost market share and improve sales of its Creative Suite software bundle, which currently has more than a 40% share of the global market.

Wednesday, August 3, 2011
Briton's EHR System - IT and Politics
Briton has been trying to create a single network that would allow NHS staff across England to access any patients’ details. A new report, however, says this will not happen now and the country has been left with a “patchwork” of costly and fragmented IT systems.
Critics claim that creating a single system was always a “massive risk” especially as clinicians were not asked for suggestions on its operation.

Click here for more.
I found the comment there that includes the following:
"One of the most basic mistakes in the public sector is to assign "IT experts" to these types of projects. That, however, is not what is needed at all - we, as suppliers and designers, have all the IT expertise required. What we need on the customer side is somebody who can write and develop correct specifications - what exactly is required, and how is it supposed to work? Specifically, we don't need young ambitious people that want to jump start a career but don't understand the KISS principle..."
I encourage the reading of the comments following the article cited in the link above.
Saturday, July 30, 2011
Tracking technology is getting smarter and more intrusive
An Online Tracking Service That Can’t Be Dodged:
Researchers at U.C. Berkeley have discovered that some of the net’s most popular sites are using a tracking service that can’t be evaded -- even when users block cookies, turn off storage in Flash, or use browsers’ “incognito” functions.
The service, called KISSmetrics, is used by sites to track the number of visitors, what the visitors do on the site, and where they come to the site from -- and KISSmetrics says it does a more comprehensive job than its competitors such as Google Analytics.
The research was published Friday, July 29, 2011 by a team UC Berkeley privacy researchers that includes veteran privacy lawyer Chris Hoofnagle and noted privacy researcher Ashkan Soltani.
It is possible, the researchers say, for any two sites using KISSmetrics to compare their databases and ask things like “Hey, what do you know about user 345627?” and the other site could say “his name is John Smith and his email address is this@somefakedomainname.com and he likes these kinds of things.”
Click here to down the research paper (2 MB pdf file) of the Berkeley researchers, read it and see what you think!
For additional insight into the tracking ecosystem, see the article "The Web's New Gold Mine: Your Secrets" in The Wall Street Journal" of July 30, 2011.

{ Click on the image above for a larger view }
And, of course, if you’re using a GPS enabled smartphone, they can add where you are now and where you’ve been to the info about you that they’re collecting . . . including where you live.
Saturday, June 11, 2011
Nobody is immune to cyberattack
The personal records of 100 million people were stolen in an attack on Sony Corp.’s video game networks. Up to 210,000 unemployed Massachusetts residents were put at risk by data theft software that infected computers at the state’s Executive Office of Labor and Workforce Development. And, in March, as mentioned in an earlier post, criminals stole vital information from data protection company RSA Security, a division of storage giant EMC Corp. The stolen RSA data was later used in a hacker raid on defense contractor Lockheed Martin Corp., an RSA client. The list of data breaches grows almost daily, and while consumers and businesses can take steps to reduce the risk of losing sensitive information, security analysts say that making our computer networks truly secure is virtually impossible.
Antivirus and other commercial security software products may be adequate against the kind of amateur hackers who vandalized websites in the Internet’s early days, but they often fail to detect the custom-made attack programs, or “malware,’’ created by today’s organized crime gangs and foreign intelligence agencies. Cybercrime by governments will probably be even tougher to fend off. In late 2009, computers at the search engine giant Google Inc. came under a severe attack aimed at getting access to the company’s software codes. A host of other companies, including Adobe Systems Inc. and Juniper Networks Inc., were also hit. In January 2010, Google attributed the attack to hackers working from within China, a claim the Chinese government rejected.

The International Monetary Fund was hit recently by what computer experts describe as a large and sophisticated cyberattack whose dimensions are still unknown. The fund said that it did not believe that the intrusion into its systems was related to a sophisticated digital break-in at RSA Security that took place in March, which compromised some information that companies and governments use to control access to their most sensitive computer systems. After that attack, the World Bank briefly shut down external access to its most sensitive systems, for fear that the stolen information could make it a target. But it quickly resumed its normal operations and says it has seen no evidence of any attacks.
Companies and public institutions are often hesitant to describe publicly the nature or success of attacks on their computer systems, partly for fear of providing information that would be useful to the individuals or countries mounting the efforts. Even so, Google has recently been aggressive in announcing attacks and, in one recent case, as mentioned above, of declaring that its origin was China, an accusation the Chinese government quickly denied.
But in the case of the I.M.F., officials declined to say where they believe the attack originated — a delicate subject because most nations are members of the fund. The attacks were likely to have been made possible by a technique known as “spear phishing,” in which an individual is fooled into clicking on a malicious Web link or running a program that allows open access to the recipient’s network. It is also possible that the attack was less specific, a case in which an intruder was testing the system merely to see what was available.
Caveat emptor.
Wednesday, June 8, 2011
HTML5 is now playing in the big leagues
The Financial Times (London) yesterday introduced a mobile Web application aimed at luring readers away from Apple’s iTunes App Store, throwing down the gauntlet over new business conditions that Apple is set to impose on publishers who sell digital subscriptions via iTunes.
A number of publishers have expressed their displeasure with Apple’s plan to retain 30 percent of the revenue from subscriptions sold on iTunes, and to keep customer data from such sales, beginning at the end of June. At the same time, mobile applications are a fast-growing source of new readers and revenue, so publishers have been reluctant to pull their applications from the iTunes store.
The Financial Times, the British daily, has tried to get around this problem by designing a new app that includes much of the functionality of an iPad or iPhone application, while residing on the open Web. It employs a new Web technology standard called HTML5, which allows programmers to create a single application that can run on a variety of devices, including Apple’s iPhone and iPad, Google’s Android system and the BlackBerry PlayBook, although the new app does not work on some versions of the devices.
The Financial Times said it would encourage users of its iPad and iPhone applications to migrate to the new app. It said it did not plan to comply with Apple’s proposed conditions, even if that meant Apple removed the existing applications from iTunes.

= = = = = = = = = = = = = = = = = = = = = =
Update on my earlier posts on SecurID tokens
RSA Security has offered to replace the SecurID tokens used by enterprises and government agencies to secure their networks after attackers attempted to hack a defense contractor’s network in May.
The SecurID two-factor authentication technology relies on a pseudo-random number that is generated every 30 to 60 seconds. Users have to enter their own username, self-selected password and the code displayed on the token. The authentication server knows what number was generated. Attackers also now know how to figure out what number is being generated, and it is easy to steal usernames and passwords using phishing or keyloggers.
There are an estimated 40 million SecurID tokens currently in use.
Click here for an open letter to RSA SecurID customers.
Wednesday, May 18, 2011
Chromebook and The Google Chrome OS
Most of the IT professionals I know scoff or snicker when I bring up the topic of Google Chrome OS. But, just as IT pros used to roundly dismiss the idea of cloud computing — and many of them are now climbing over each other to tout their cloud and virtualization expertise — it might not be long before IT also warms up to Chrome OS, out of necessity.
Over a three-year rental period, a business would pay $1008 for a Chromebook, plus another $150 for Google Apps. That’s roughly about the same cost most businesses would pay Microsoft for a seat of Windows, Microsoft Office, and a CAL for Microsoft servers (as part of an Enterprise Agreement with Microsoft). However, with the Google deal, the company also gets desktop hardware and it can eliminate or at least greatly reduce most of the expensive server hardware and backend Microsoft software. For many businesses, that kind of equation would be very lucrative and way too tempting to ignore.

Click here for YouTube video.
Tuesday, May 17, 2011
Using The jQuery Mobile Framework - Write Once, Publish Anywhere
As described in earlier posts, the emphasis in Dreamweaver CS5.5 is firmly on mobile development and designing for multiple screens. A big part of this capability comes from its inclusion of jQuery Mobile, a sophisticated JavaScript and CSS framework designed to work consistently in all major mobile platforms.
•Apple iPhone/iPod Touch
•Google Android
•RIM BlackBerry/Playbook OS
•Nokia Symbian (retired, but still with over 1 billion users worldwide)
•HP/Palm WebOS
•Microsoft Window Phone 7
Built upon the popular jQuery JavaScript framework, jQuery Mobile lets Web designers and developers build mobile application interfaces quickly and consistently. Dreamweaver CS5.5's jQuery’s mobile strategy can be summarized simply: Delivering top-of-the-line JavaScript in a unified User Interface that works across the most-used smartphone web browsers and tablet form factors.
Click here for an introduction to jQuery from Adobe.
Click here for an introduction to jQuery Mobile from Adobe.
Click here for the jQuery Project site
Click here for the jQuery Mobile Project site
Friday, May 6, 2011
Building Mobile / Phone Apps with Dreamweaver CS5.5 and PhoneGap

Seamless integration of the PhoneGap and Android SDKs into Dreamweaver CS5.5

PhoneGap emulator with my app (The one with the red check)

My Dreamweaver CS5.5 mobile app running in the PhoneGap emulator
With PhoneGap, you can write a mobile app using standards-based technologies (HTML, CSS, and JavaScript). You can add device-specific functionality, such as multitouch, geolocation, and accelerometer features. To finish up, Dreamweaver assists you in compiling and packaging the app for direct delivery to the device or to vendor-specific online app stores.

The PhoneGap emulator phone

{ Click on any of the images for larger view }
Friday, April 29, 2011
Using jQuery. HTML5, PhoneGap And More In The New Multiscreen World
The soon-to-be-released Adobe Dreamweaver CS5.5 (part of Creative Suite 5.5) helps you create content with HTML5, CSS3 and the JQuery mobile framework (among other things) and target multiple platforms including Android operating systems, iOS, and Adobe AIR. As seen in the images below, Dreamweaver CS5.5 reflects the new and growing presence of not only the desktop computer, but the smart phone and tablet as well.

{ Click on any of the images for larger view }
With the Dreamweaver CS5.5 Media Queries dialog box, you can attach or create CSS files for different screen sizes and force devices to report their actual widths.

PhoneGap

With the Mobile Applications feature and the SDK for Android (shown above) or iOS, you can emulate and create a native mobile application from your Dreamweaver CS5.5 site files.

PhoneGap is an HTML5 app platform that allows you to author native applications with Web technologies and get access to APIs and app stores.

To streamline your projects, the PhoneGap framework is now integrated as an extension in Dreamweaver CS5.5. So, using PhoneGap, you can build native Android and iOS apps directly from Dreamweaver CS5.5 projects.
Adobe has proven that it can work intimately with a vendor, such as with Research in Motion, whose application development strategy for the PlayBook at launch is 100 percent dependent on Adobe’s AIR and Flash technologies (and will be so until other native QNX SDKs and “Players” are released). Today, the PlayBook demonstrates excellent performance with the Flash and AIR runtimes as both stand-alone tablet apps and embedded into a Mobile browser.
Click here for a look of the Blackberry PlayBook runing video using Flash and HTML5. Video on the PlayBook is superb, with crisp resolution. Video arguably looks better on the PlayBook than on its iPad 2 and Motorola Xoom rivals.
At the same time, on the iOS platform, users aren't feeling any lack of Flash. Virtually every Web site imaginable has moved to HTML5 H.264-based encoding of embedded video. YouTube itself has also fully optimized itself for Mobile Safari and iOS. So, as I've been pointing out, to compensate for this shift, Adobe has introduced HTML5 support into its tools.
More to follow. Stay tuned.
Saturday, April 16, 2011
Developing Rich Web Apps On A Network With Many Platforms (JQuery Mobile)
jQuery mobile framework takes the "write less, do more" mantra to the next level: Instead of writing unique apps for each mobile device or OS, the jQuery mobile framework will allow you to design a single highly branded and customized web application that will work on all popular smartphone and tablet platforms. Click here for more.
Basic features of jQuery Mobile include:
General simplicity
The framework is simple to use. You can develop pages mainly using markup driven with minimal or no JavaScript.
Progressive enhancement and graceful degradation
While jQuery Mobile leverages the latest HTML5, CSS3, and JavaScript, not all mobile devices provide such support. jQuery Mobile philosophy is to support both high-end and less capable devices, such as those without JavaScript support, and still provide the best possible experience.
Accessibility
jQuery Mobile is designed with accessibility in mind. It has support for Accessible Rich Internet Applications (WAI-ARIA) to help make web pages accessible for visitors with disabilities using assistive technologies.
Small size
The overall size of the jQuery Mobile framework is relatively small at 12KB for the JavaScript library, 6KB for the CSS, plus some icons.
Theming
The framework also provides a theme system that allows you to provide your own application styling.
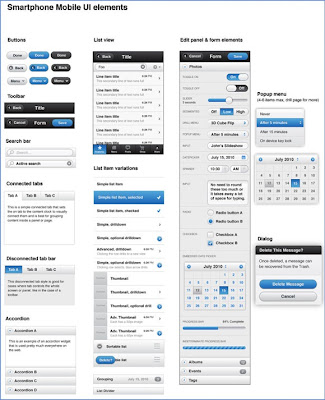
Some jQuery Mobile UI elements
But getting back to Adobe Creative Suite 5.5 Web Premium: with it, you can:
- Manage content for different screen sizes.
- Develop apps for virtually any mobile device.
- Ensure design integrity across the entire web.
For a look at this new flexibility, click here to watch Adobe's Dreamweaver CS 5.5 creating a rich app for Apple's iPad.
Stay tuned!
Wednesday, April 13, 2011
HTTPS, Certificates and Web Security Reconsidered
The Comodo Group, an Internet security company, has been attacked in the last month by a talkative and professed patriotic Iranian hacker who infiltrated several of the company’s partners and used them to threaten the security of myriad big-name Web sites.
But the case is not a problem for only Comodo, which initially believed the attack was the work of the Iranian government. It has also cast a spotlight on the global system that supposedly secures communications and commerce on the Web.
The encryption used by many Web sites to prevent eavesdropping on their interactions with visitors is not very secure. This technology is in use when Web addresses start with “https” (in which “s” stands for secure) and a closed lock icon appears on Web browsers. These sites rely on third-party organizations, like Comodo, to provide “certificates” that guarantee sites’ authenticity to Web browsers.
But many security experts say the problems start with the proliferation of organizations permitted to issue certificates. Browser makers like Microsoft, Mozilla, Google and Apple have authorized a large and growing number of entities around the world — both private companies and government bodies — to create them. Many private “certificate authorities” have, in turn, worked with resellers and deputized other unknown companies to issue certificates in a “chain of trust” that now involves many hundreds of players, any of which may in fact be a weak link.
The Electronic Frontier Foundation, an online civil liberties group, has explored the Internet in an attempt to map this nebulous system. As of December, 676 organizations were signing certificates, it found. Other security experts suspect that the scan missed many and that the number is much higher.
Making matters worse, entities that issue certificates, though required to seek authorization from site owners, can technically issue certificates for any Web site. This means that governments that control certificate authorities and hackers who break into their systems can issue certificates for any site at will.
Experts say that both the certificate system and the technology it employs have long been in need of an overhaul, but that the technology industry has not been able to muster the will to do it. “It hasn’t been perceived to be a big enough problem that needs to be fixed,” said Stephen Schultze, associate director of the Center for Information Technology Policy at Princeton. “This is a wake-up call. This is a small leak that is evidence of a much more fundamental structural problem.”
In the Comodo case, the hacker infiltrated an Italian computer reseller and used its access to Comodo’s systems to automatically create certificates for Web sites operated by Google, Yahoo, Microsoft, Skype and Mozilla. With the certificates, the hacker could set up servers that appear to work for those sites and try to view the unscrambled e-mail of millions of people, experts say. Comodo says it has suspended the Italian reseller and a second European reseller that the hacker also infiltrated.
In a series of online messages teeming with bravado, the hacker described himself as a software-engineering student and cryptography expert and said he worked alone. He suggested he was avenging the Stuxnex computer worm, which was directed at Iranian nuclear installations last year. And he indicated that he intended to use the certificates he created to snoop on opponents of the Iranian regime. “As I live, you don’t have privacy in Internet, you don’t have security in digital world,” he warned.
The certificate system was created at the dawn of e-commerce in the early 1990s before security was a major issue. Security experts say the system is not up to the challenge of today’s immense, commercial and much-attacked Internet. It was designed primarily to let businesses take credit card payments online, and less to confirm the authenticity of Web sites.
The crucial tool available to Comodo and the browser makers — revocation — is ineffective, security experts say. After the Comodo case, Google, Mozilla and Microsoft rushed out patches so their browsers would recognize and reject the bad certificates. But this solution requires many millions of Internet users to update their browser software, which many people never do.
Moreover, because certificate authorities’ servers are seen as unreliable, most browser makers allow users to proceed to an alternative site, and hackers can exploit this weakness, security experts say.
Browser makers have another problem: Faced with a suspicious certificate authority, there is little they can do shy of rescinding it. But if they did that, millions of Web users might encounter troubling error warnings when they visited sites with certificates from that company, causing a cascade of problems for users and site owners. Cutting out a large player like Comodo, which controls at least 95,100 active certificates, could effectively “break the Web,” said Dan Kaminsky, chief scientist at the security firm DKH.
They are effectively “too big to fail,” said Christopher Soghoian, a former Federal Trade Commission technologist who is now a graduate fellow at the Center for Applied Cybersecurity Research at Indiana University. “The problem is that the browser vendors don’t have a small stick, they only have a big stick." He said he could not recall a single instance in which the browser vendors had rejected a certificate authority.
Microsoft and Mozilla said that they would consider removing certificate authority if it was in the best interest of Internet users, and that they remained in talks with Comodo about its security practices. “Participation in Mozilla’s root program is a privilege, not a right,” the company, the nonprofit maker of Firefox, said. Apple, maker of the Safari browser, declined to comment. (Google’s Chrome browser defers to the choices of operating system makers like Microsoft and Apple about which certificate authorities are accepted.)
Mozilla, Microsoft and Google said they would work together and with certificate authorities and the security community on improvements to the system. One approach proposed by Comodo and Google engineers in January would allow Web site owners to specify which certificate authorities may issue certificates for their sites.
An initiative preferred by security experts would overhaul the system more radically. It would give Web sites similar control while securing their certificates within a new encrypted version of the domain name system, the central directory of the Web, making it the de facto central certificate authority through which Web sites could generate their own certificates.